Introduction
The delicate data that businesses store is at risk more than ever by malicious attackers in today’s Internet driven world. Notably, as more companies turn to cloud and mobile solutions to help optimize business practices, it’s crucial for these businesses to consider the vulnerabilities that tag along with these technologies to ensure their data remains safe.
When companies fail to put security measures in place to combat these threats, it often results in a breach which they can’t recover from financially. Recent studies on the costs associated with a data breach have shown the average cost of being a victim of an attack to be around $4.4 million. In an ever evolving technological race of trying to secure sensitive data verse those working to break that encryption, how could a company possibly block all the unknown threats?
While all cyber threats can’t be foreseen or prevented, implementing strong security standards and policies is critical to avert potential data breaches.
Downfall of BYOD
One area often overlooked in security involves companies that allow employees to use their mobile devices for work functions. This practice is referred to as Bring Your Own Device, more often called BYOD.
Since more companies are starting to follow this methodology, hackers are eagerly refining their techniques to crack the exploits of mobile devices. While allowing employees to use their own devices affords companies obvious cost benefits, it allows for less control on the security of the device.
Unless a company enforces strict standards on the hardware’s software updates, installed applications, and password protection, employee devices can leave a hole wide open for hackers into a company’s network. In addition to the risk of software exploits, no device's security offers protection against the physical theft of a user’s mobile device containing their company’s secure data.
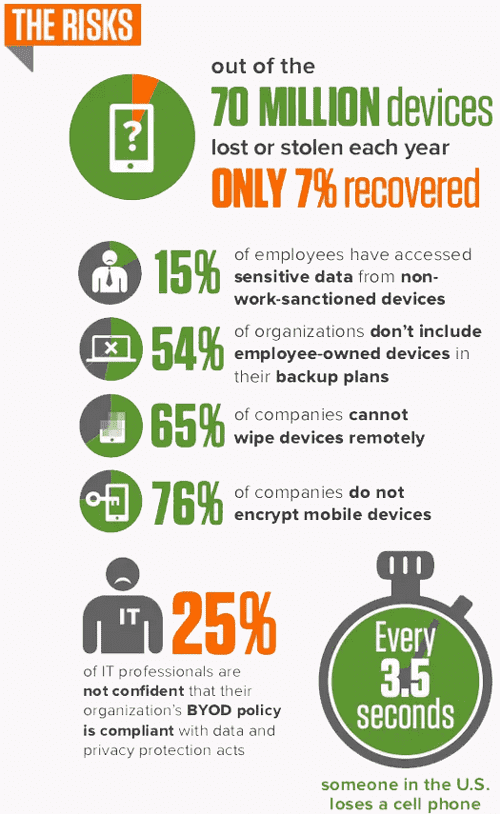
The theft of personal devices that contain sensitive data has cost many businesses to lose millions of dollars in fines and law suits. For instance, a hospital was recently fined $1.5 million when a laptop was stolen with unencrypted data on patients and research subjects.
Even though unsecured mobile devices can become a big concern for companies, most security threats can be mitigated by implementing smart mobile policies and providing security awareness training to employees.
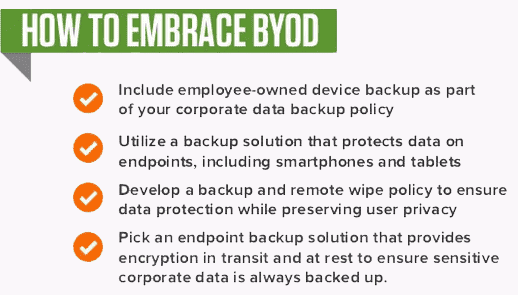
Vendor Breaches
Regardless of the controls companies put in place to prevent data breaches through mobile devices, there is always the threat of an attack through the vulnerabilities of partners and vendors connected to their network.
In today’s industry, it’s common for companies looking to reduce IT overhead to outsource various business processes to third-party vendors.
However, it’s critical for enterprises to ensure that the potential vendor has a strong security policy in place. When a third-party service provider has low-security standards, it makes them an easy target for attackers to use to piggyback into a target enterprise.
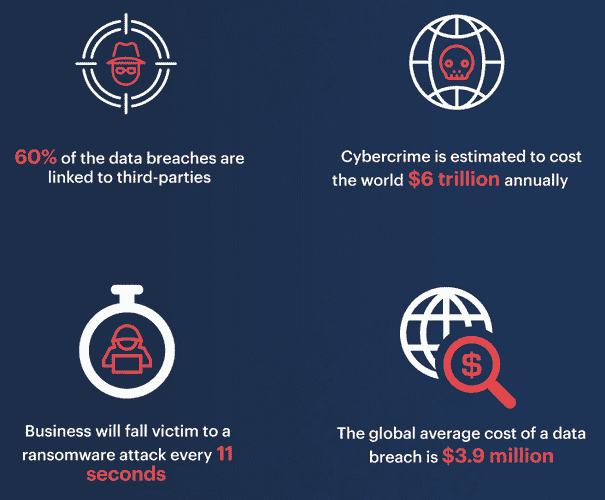
A report performed by Trustwave Global Security notes that security exploits found in the networks of third-party vendors account for around 62% of all data breaches. In the aftermath of a breach in any partner or vendor networks, it’s imperative for a company to update their security measures to protect from hackers using the information gained in future attacks.
To emphasize the severity of this threat, in January of 2016 the IRS announced that it had fallen victim to a malicious attack that was using Social Security Numbers, gained from previous attacks outside the IRS, to generate e-filing PINs that could potentially be used in future identity theft or social engineering attacks.
With the threat of third-party network breaches in mind, companies need to enforce security standards across any and all parties connected to their network.
Malicious Intent
No security is invulnerable and due to how persistent hackers can be, a malicious attack is inevitable.
The research of IBM and Ponemon Institute concludes that the root cause of most data breaches is caused by malicious attacks around 48% of the time. While security policies can be placed on a company’s network and any connected partners, it hard to halt an ever evolving opponent trying to stay a step ahead of the security industry.
Malicious software can attack many fronts to infect an enterprise’s workforce through negligent employees or contractors using a variety of harmful tools, such as spear-phishing campaigns, spyware, fake technical support scams, ransomware, zero-day exploits, Trojans, Potentially Unwanted Programs (PUPs), and social spam.
As a result of this imminent threat, it’s critical for an enterprise to stay up-to-date with software patches, as well as train employees on security policies and how to identify malicious attacks.

Conclusion
Ultimately, there is no guarantee that an enterprise can avoid a breach into their sensitive data. However, following strong security practices greatly increases the chances of fighting back potential invaders.
For instance, most attacks targeting mobile are nullified with mobile device management solutions, BYOD policies, and educating employees on mobile threats. Or how updating security measures after a breach into a partner or vendors network will prevent harmful after effects. As well as simply keeping software up-to-date and training employee on how to detect malicious content.
Battling such a persistent threat requires a company’s securities standards to be just as persistent in fighting back potential breaches.
What are your thoughts on the security issues organizations face today? Did we miss something more imperative than these three security concerns? Please leave your feedback or comments below.

